Since I’ve never found a complete and easy tutorial on how to setup an encrypted account using the default macOS/iOS Mail.app, I’ll try to explain my setup and how I made this. Keeping things separate for the two type of encryption, an easy and less secure way: S/MIME, and the more robust and secure PGP. I’m using both on my macOS/iOS devices, with two different apps, when I want to use a friendly way and I don’t have to share important information, I I use the handy S/MIME with the default apps, and when I want to have a robust encryption, I switch to another app with PGP encryption. Both the apps are easy to use and don’t require specific capacities.
Before the beginning, I want to write about why I choose this two ways. The S/MIME encryption I don’t think is the best secure way because you have to trust a third part certificate authority, but I use it with my parents/girlfriend/friends, in order to have more privacy, to sign my account and to hide the content of my emails from Google services (they already have many information about me without my emails…)
The PGP one is more robust and safe because you generate your private keys locally on your device and there are no other external services involved.
Starting with a little advisor: this post will be a bit long and tricky, is not a difficult thing but is long in order to report all the things in the correct order and explain all well, so I hope to don’t make errors in the timeline of the various steps.
First we need to know how and end-to-end (E2E) encryption works, but I will not explain it, because I don’t have the abilities and the web is full of these info, this article for example.
Second, I’ll start with the more easy and friendly S/MIME, then PGP with RSA keys. So jump to the end if you want to jump to the last steps.
S/MIME encryption
In order to get S/MIME encryption works, you need to get a certificate from a third part service, there’re a lot of these services, I used the free one from Actalis (Actalis is an Italian S.p.A. owned by the italian IT S.p.A. Aruba, should be quite reliable). So, get your S/MIME certificate from here, is pretty easy, just write your email, get an email with the verification code, then input the verification code on the Actalis portalis, and after you will receive your S/MIME certificate back in an email. Remember to save the password that will be used to open the .pfx certificates and install it on your macOS. You can change the password after by login in Actalis portal. And this is why I don’t trust so much this way…
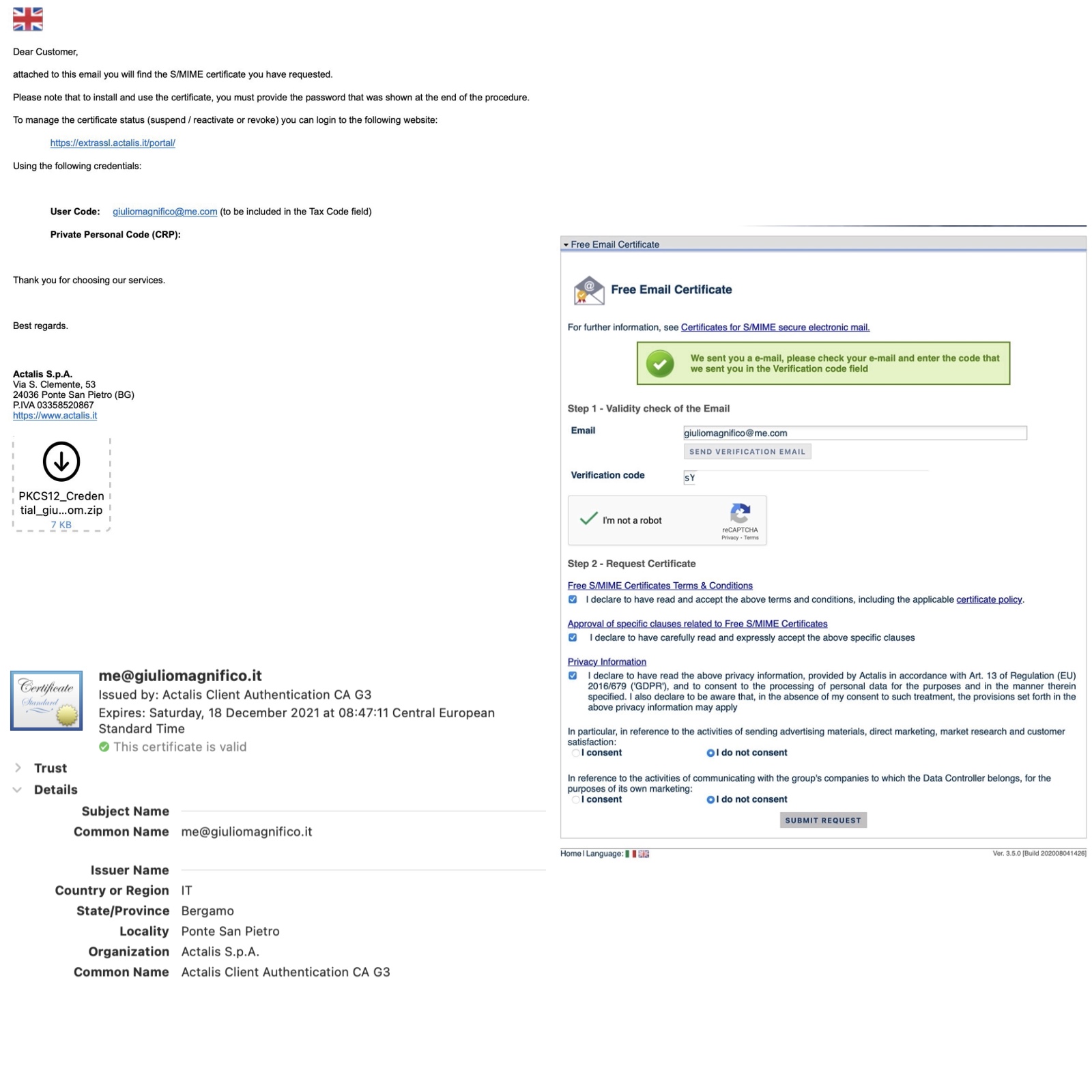
After made these simply steps our emails sent from that address will be certificated (and encrypted if the person who will receive them, has our public key/certificate).
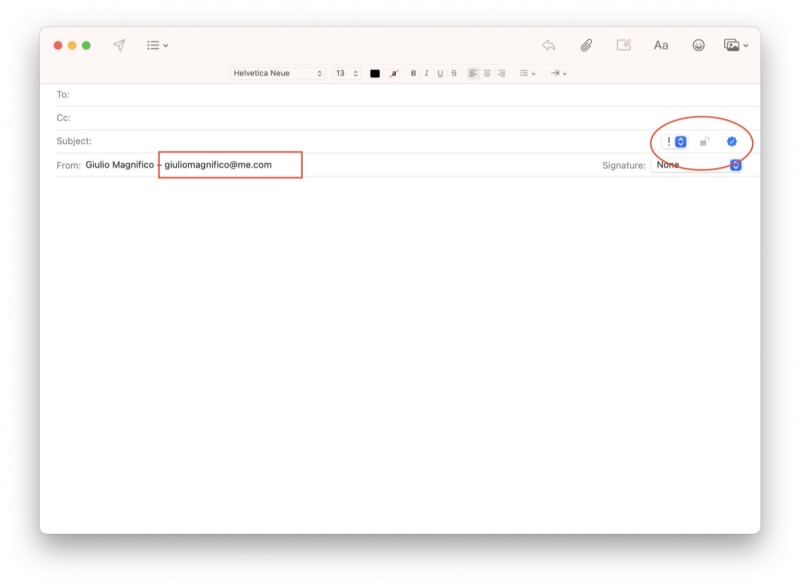
(This is an email that I don’t use, it’s just for writing this article). Then the tricky steps in order to send and receive encrypted emails: install your certificate on all your iOS devices, and you have to do the same on all your devices from where you send the mails and on the devices that will receive the mails. Just to explain I’ll do it on my another email, but you have to do, or tell the people to do it, on all the other devices, otherwise the mails will be signed but not encrypted as you can see from the image above (the lock is open).
Now export your certificate in .p12 format and put it in your cloud folder (or send it by another way, like email, you need to have access to it on your ios device) and install it by simply tap on it, you will see a new profile in your Setting.app.
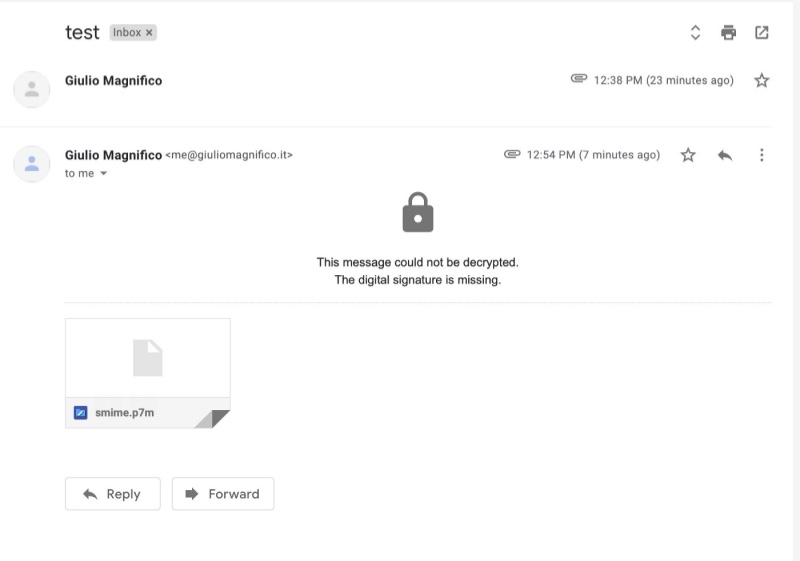
Because if you don’t do it and, you send an encrypted email to other people, they will not be able to see the content
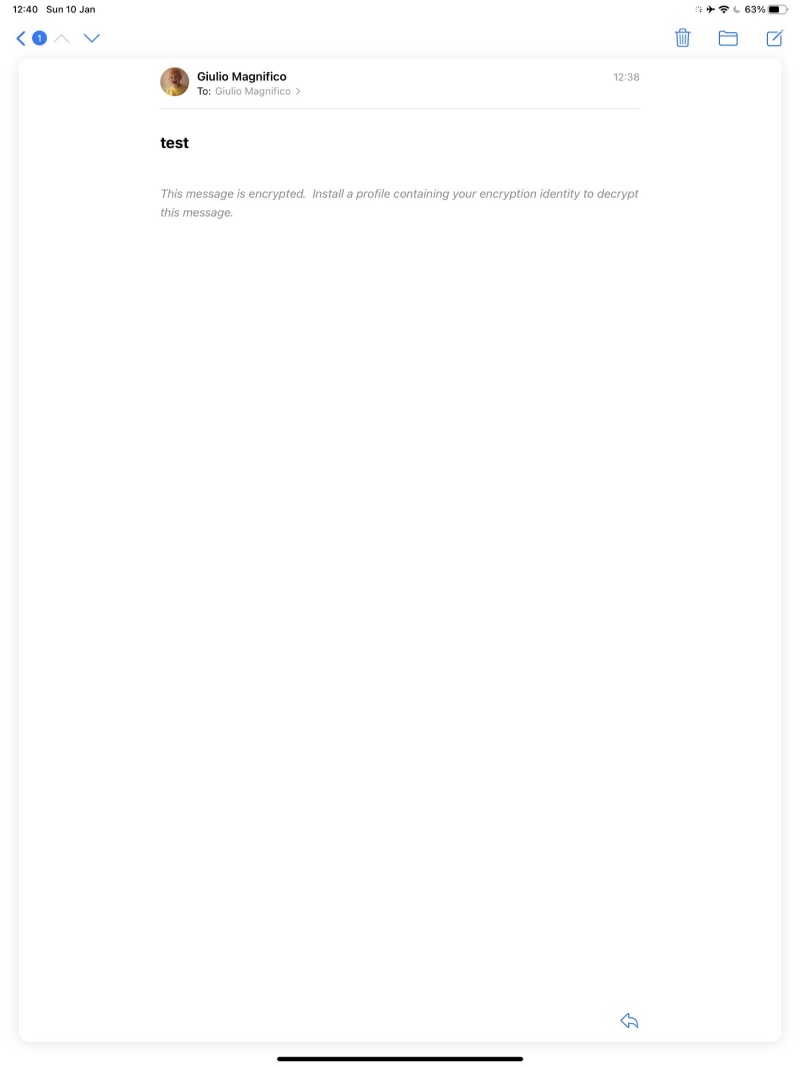
Well, now you should have a new profile installed on your iOS device (I’m using my iPad Pro for this test)
After this you have to say to iOS Mail.app to use this certificate and encrypt new emails with it (when the encryption is available of course), so go in Mail > Accounts > your_account > Advanced > S/MIME > check both the options, Sign and Encrypt
Now back to the previous email, and now you will be able to decrypt/read it, and you will see the fancy icons on top =) (the badge is for a certificate email and the lock icon, …well you aren’t stupid!)
But if we want to reply? No problem but untill we install the certificate we will not be able to encrypt the mail, because we have our certificate but not the one from the sender email,
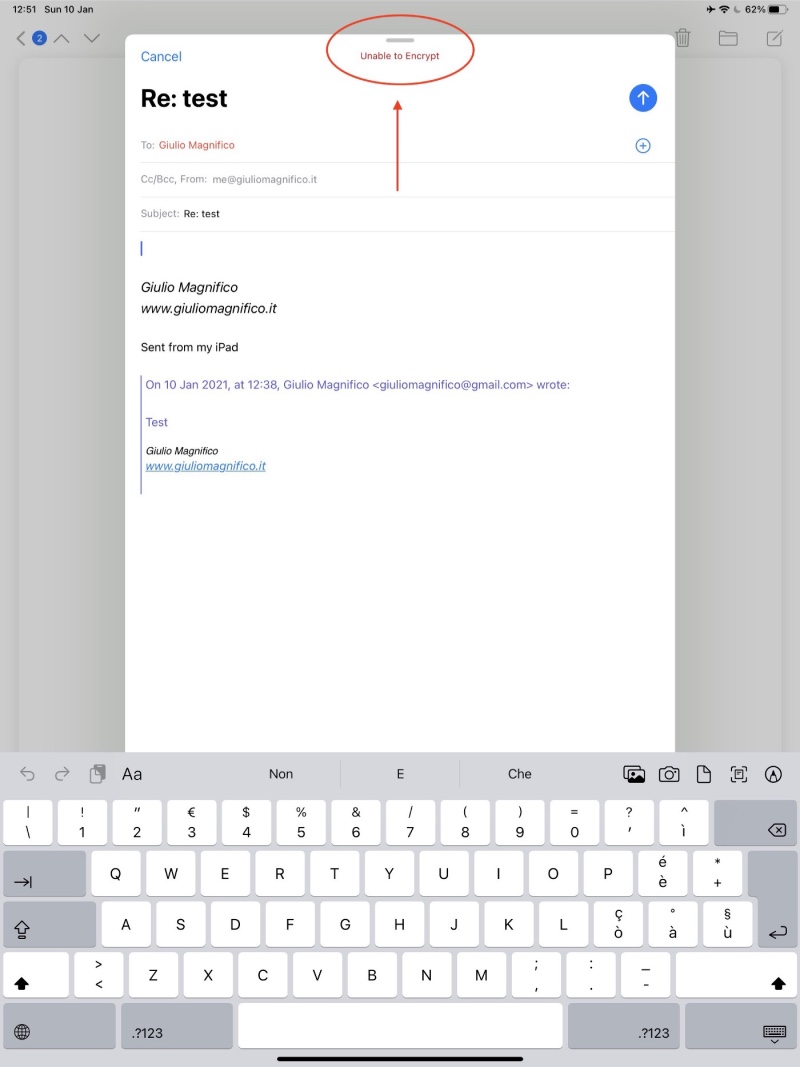
in order to do this, you don’t need to send again the certificate via iCloud or blabla…. iOS is pretty smart and you can install the public key of the sender just by tapping on his name
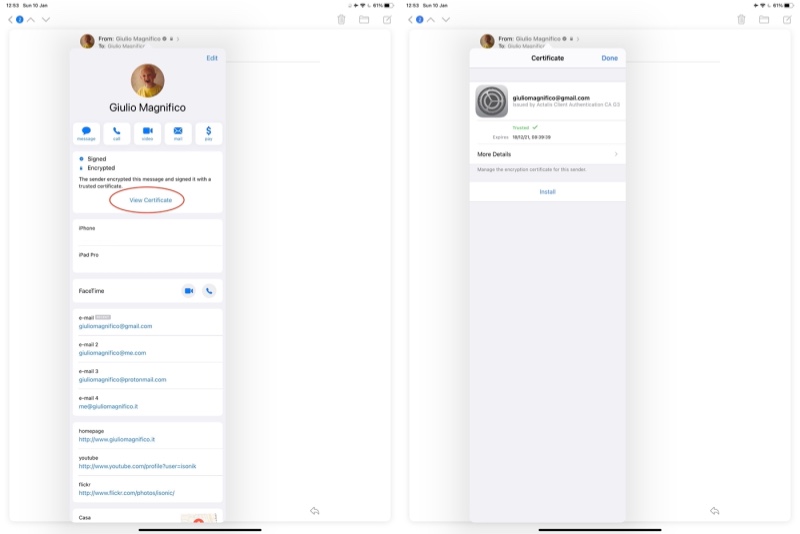
You can send a message in order to test it on Mac, the email should be signed and encrypted
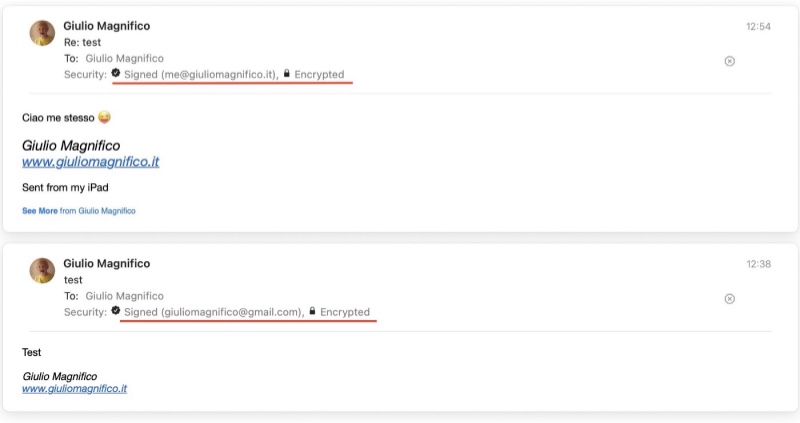
All done, this is the easy way, now your email are encrypted, remember to tell the other people to install your certificate/public key or you will not be able to send encrypted mail to them.
Now Google services will not be able to read the content of email, it’s just a privacy purpose in my case, because I don’t like that Google is scraping my email in order to profile and get more info on me.
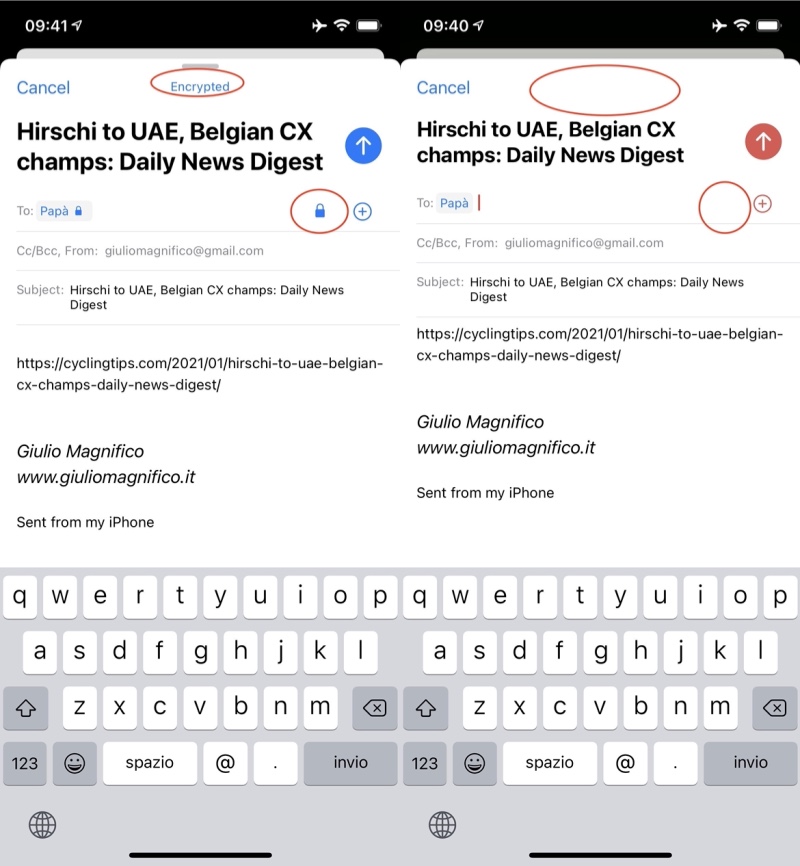
But an important thing to consider is that on iOS the emails sent via other apps, that is not Mail.app, are not encrypted, you have to save the drafts and then send them via Mail.app. This is pretty annoying because usually I send a lot of email from my RSS app or browser… but there’s nothing to do at the moment. Same email from Reeder.app, saved as draft and sent back via Mail.app:
PGP encryption
Now the more secure way: via PGP. In order to do this, you need to have installed Homebrew on your Mac, or use the Mail.app plug-in GPGtools. Since I’m not “a fan” of GPGtools, not because it has something wrong but because it installs a lot of things and features, not only the mail plugin but also some backgrounds login items, contextual menus, etc… and I’m a minimal guy, I don’t want not indispensable software on my Mac. You can disable some login daemons of PGPtools if you want, and it still works as Mail.app plugin only, but you have to pay, to install it, in order to use only a simple plugin, and I don’t want to use Mail.app on my macOS to encrypt/decrypt pgp mails, I prefer to keep the things separate like on iOS, indeed I’m using Thunderbird on macOS and PGPro on iOS.
As said, you need to install Homebrew, it’s very easy, and I don’t want to write a guide about it, once installed you need to install gnupg (the open source GNU licensed PGP) software via
brew install gnupg
When the installation is done, you need to create you key
gpg--gen-key
The default options should be good for you (it’s 4096 bits RSA key), if you want more detail use the gpg — full-generate-key command and follow the easy instructions
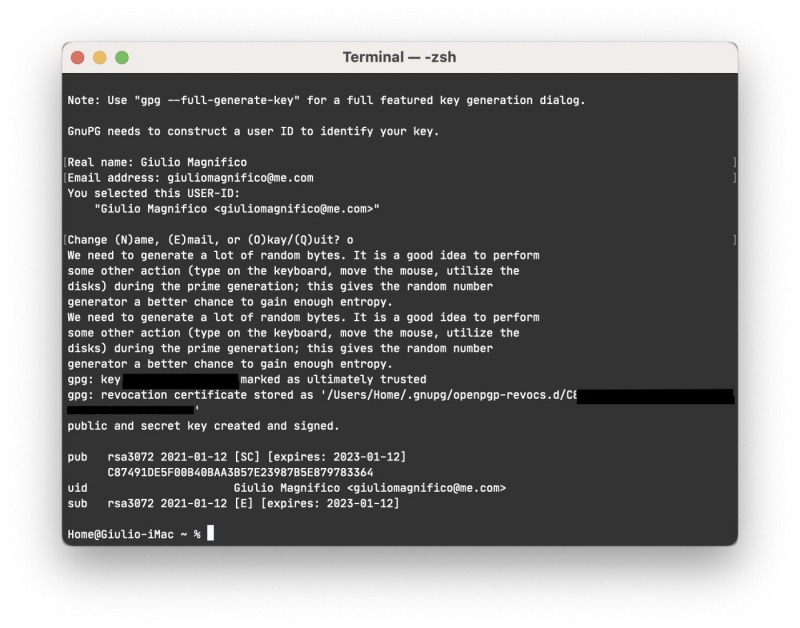 Now you should have your key, use this command to see the just created key, in order to see if you haven’t made errors
Now you should have your key, use this command to see the just created key, in order to see if you haven’t made errors
gpg --list-keys
Then we need to use it on iOS using the app PGPro, because this encryption is not available with the default Mail.app. There’re two ways to import and use it to the iOS app PGPro, one is to upload the public key to the MIT servers, the other is by sending via clipboard or similar.
To upload it to MIT server
gpg --keyserver pgp.mit.edu --send-key ID
Where the ID is the key number of your key listed before, should be a number like C87491DE5F00B40BAA3B57E23987B5E879783364
Home@Giulio-iMac ~ % gpg --keyserver pgp.mit.edu --send-key 7C24F2C91EE4BDF584568A9E32CBBFF768F54896 gpg: sending key 32CBBFF768F54896 to hkp://pgp.mit.edu
You can search your key via browser at pgp.mit.edu or via CLI using “gpg — keyserver pgp.mit.edu — search-keys ID” but at the moment the MIT server returns me a 503 error/gpg: error searching keyserver: No keyserver available, so I’ll do it via copy/paste. So I’ll not use this way and instead I’ll esport both my public and private key using this commands (I’ll do it for my gmail key)
gpg --armor --output key.txt --export giuliomagnifico@gmail.com gpg --armor --export-secret-keys giuliomagnifico@gmail.com > privkey.asc
Open both the files with TextEdit and copy all the text inside the public key, go on PGPro app on you iPhone, keychain tab and import the publick key via shared clipboard. Do the same for the private key (copy all the text and import to PGPro app)
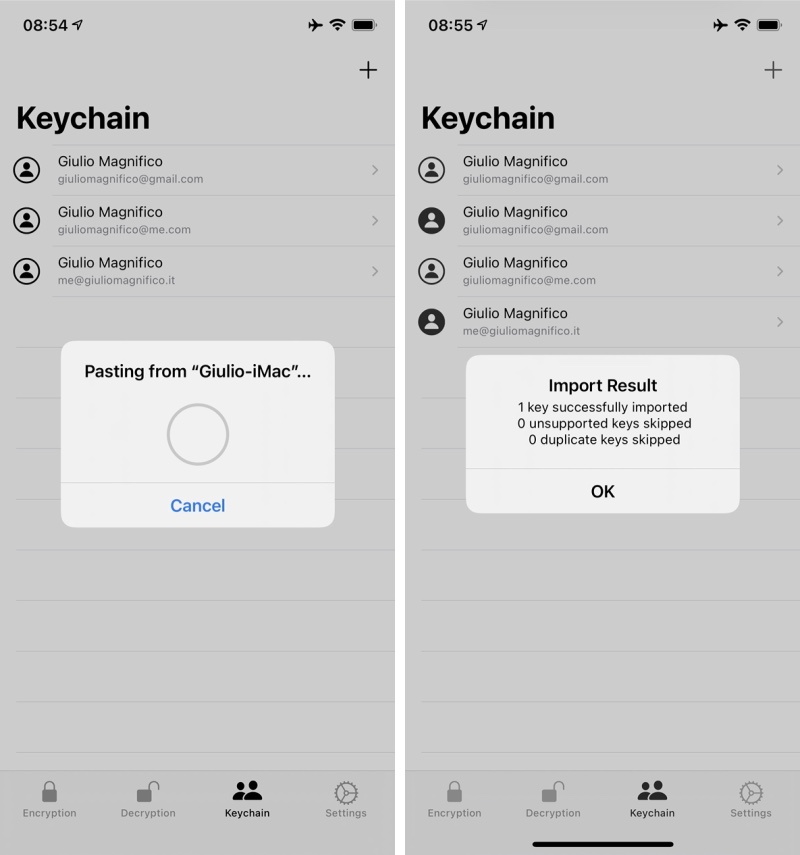
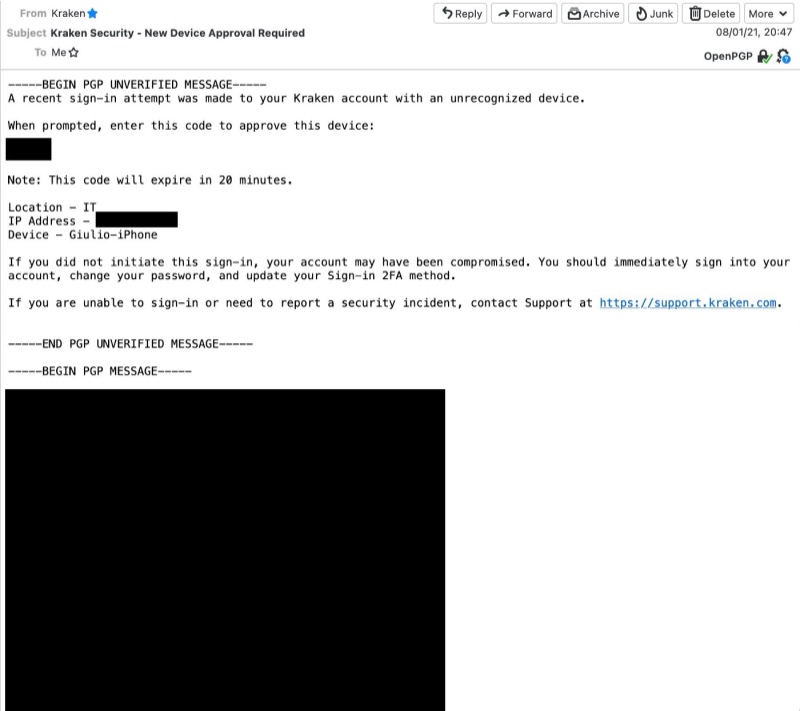
Now you are able to encrypt/decrypt a message via PGPro, in example I want to decrypt an old message sent from Kraken exchange to me, go to Decryption tab, select the private key of the account where you have received the mail, write the private key password, paste the PGP message from Mail.app and tab the mail icon, et voilà:
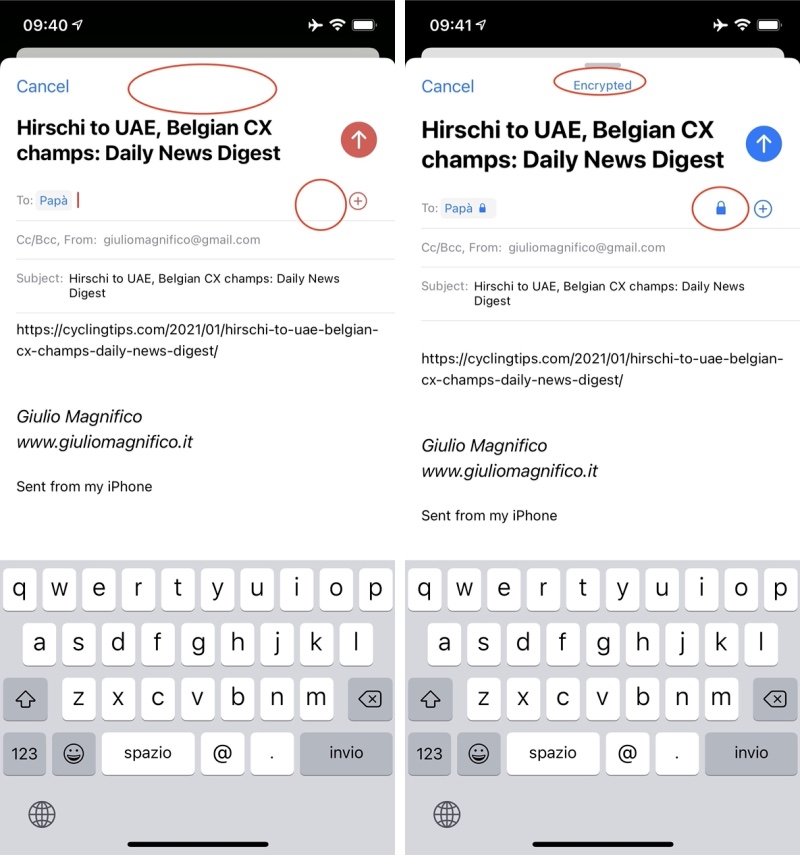
In order to encrypt a message is the same process but in encryption tab and with public key only. Moreover, in the Preferences of the PGPro you can choose if you want the “Mail integration” or not, if yes, once the message is encrypted the app will automatically create a new mail, I’d rather not use it because I may want to send the message via other app. I’m also using the FaceID authentication (this is one reason why I want to have two separate apps for more secure encrypted email).
Now all is done on iOS device, but we still need to read the message on macOS, also there are lots of options, you can use the Terminal using the command (where mail.txt is the content of the pgp mail)
gpg -d mail.txt
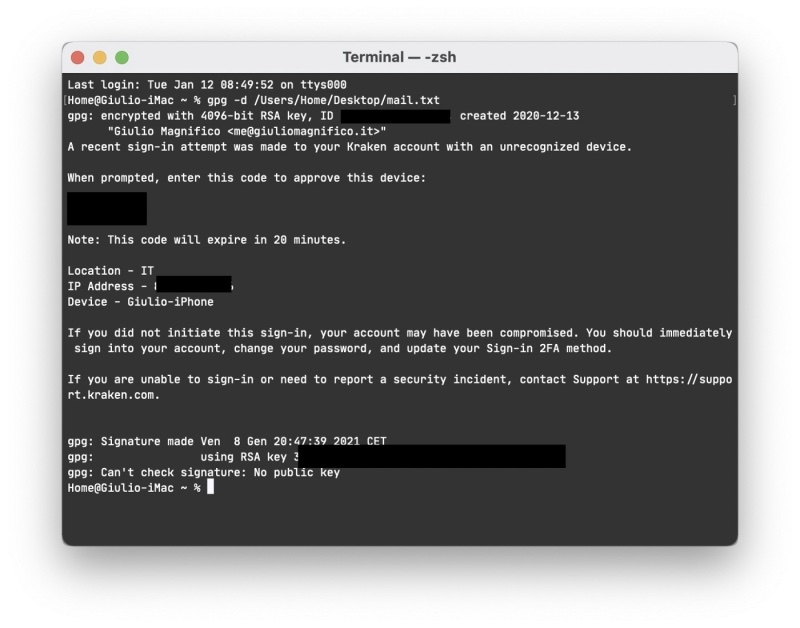
But it’s not beautiful and comfortable, I prefer to use an app with a GUI, so Thunderbird is my choice. As said before in this article, you can use also GPGTools if you want to use the default Mail.app on macOS. I don’t want. And since from Thunderbird 78 the PGP encryption is integrated in the app, you don’t need to install and trust other plugins. In order to setup the Thunderbird client you can follow the official guide, is pretty easy: OpenPGP in Thunderbird — HOWTO and FAQ
And here we go with the same mail
That’s all and I hope without errors/misunderstandings, if you want to send me an encrypted email with all your segrets =) here’s my public key for the email me@giuliomagnifico.it
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQINBF/WctABEADRvQZqe5LFiJ2FPfvciFHFmf4WBX6b/Er0kkIK7kGTjCtvFIfa
8te+7it/TB+DX5JLmnf1gQNGi5haRJJNvWw4hnyMfDjo1N8zoQRXdjGdP1yiw7fH
r3ms2txsfD3LZPGDDDIyzeLipGRH7SxYg6nmpvgAuamuKuG0wiISRIe5pqkhbcgY
1iv0RsSU4sDslmtu1cpZIWKhGArMLz+R2ZiUYKZxAJvVRNYQAoHNA2f7/lgpKmg3
B8GkIAoaioWd/E1kr3QSVw3ESFVS6bOClY5f6PMEpERNBDRQ/irglHYRwtftiWOA
63W9pQnXMD2rZoDMCPdGSbGRYNkWylYJDcOk064uDoAb9vdPB/gKdnW/5JY9mZkr
WqhzFrRRLwOX9BxuKnLT+iTTupbT+iNTjCaedQc12MLLjW+HgPi3u6qh5z9GfbYq
SZ8HiZGWcLpxjHogWhZIV2vSQHo1GCan6y0ZKZFLuZCj78gpkBGCJwr7D4gnhJLn
fSjMYl2tQj/OX5ajw87/ip/X4vV4+Ri8T/pydkBLJ0jKwvWl5qMFgllY3bxtFMir
QmHWF8z3c8jsoqbsBRttZCNFhFLkfEUYRA8SvROxxBBLRTycLx5LIR+Xjb4RRCWd
uhAoEbvmMbr04vI5WeAg/Ns6l91h4QW14ohIixNREQ8cXAw1Ne/At1EpzwARAQAB
tChHaXVsaW8gTWFnbmlmaWNvIDxtZUBnaXVsaW9tYWduaWZpY28uaXQ+iQJOBBMB
CAA4FiEEDy3Rj+Bre+uzWv1M8H0aYoPEArUFAl/WctACGwMFCwkIBwIGFQoJCAsC
BBYCAwECHgECF4AACgkQ8H0aYoPEArXlFg/8CQydaRu9ztW6/ADWgQDvC4L1v2Fg
Qu11L9uETy+rd3j2v5so6Zc++OY3gmBZgPSa3ukZa0qlgcfux6x/UdnG93sSUYD2
rWhGf4HOm8K+ofPrwdARxSUnDZiAq8+u5ZZkdYAh2fMRECxDeI5QuvhEq2OmezVl
tsUMrC77a4PbioqZWkKYSFgh9nDsixRsFmVJuNDVVOzF4n/Agmnz9+lvxDCuKfzH
QngP/1LojZ7YjS+KGS0kZrDzOml5LsG6wvmU1/qWqmon3mWjRkfeUk1o3De449oO
ZLeuaoDRyjaQynXQv16/OIUiVwW1bvH9E2cCpqYjsKc5NA/KTd7plh8JeWabgumK
PB5mTkOI6ekl5VLSTl9H2sZJZXAP3NFksGFAph4gMyY4X3lRC4/VYk8Rw3Cf1oX1
fSCNsfKNg3A5yH50HY7/8s87hU3RSatRv1w02+mzYgeUPEbwdegpsSR61h4HsklW
NBVgjJWqwMPLpAi+NNFtnDlfHcj0TNBC99oNx/pEYxV6xXbwrt/+gA4QulU/XrrA
FhPnSa4WTZQlxZX6BrjG24UNfoNrwVIeE4I5YLrI6ONYNs9PE8kvz7Ldpt08jpLB
7q11ZySmX4sl7DqVmv5QOLh6ZaQQpsQ4cdbo0O0wZiUCEZumaVf6fUES9waSk8Ma
qBkeOcQhTb3dGne5Ag0EX9Zy0AEQAMLd/vNQt6N6ZQuikp/IMAID57uXzfLUOpmA
5vt9uPWS9a7wvJtTH3OE2kgTUyLOPSYtoGkAtooGK46tucXmitF/BCbZRYUV3YAr
ANevbCuIPbQscwRturFIpOU3UmVq1YpcxAMWFTm8bsciYTLTuOMFlSfUOl4dzcfT
8zuzc14TX8XwfLzqSMvYnZAsnE7SoBReXhfBO3cfy+ewUqHiTC789uRnndJVVsQq
05qkDQ9AFDmypSpiYek5Hdd+VzTux9bs6rgON3g4vf0Ak2yXr0/lbICFi3oVEOsD
wNe7tGpJtBOG5Rj1sQOOS12AJurVTJvW6yV6wIlEbd4vKyNz9vbY+g9KNxPbPexV
9ldGzYmFcI9UvLnkZLvRDMLcX3Rl+UhkJXLHXdUGXId2nrwUrdkJBZ66KYciowO9
oZRwlb/VeResMHSUfePMEgUd+9ZRqkEYV/bHGp3bEsg1bdEugHt3oNOM2FNwz9uH
qUruWxV2eazWhmfqywR421jWEnUKiqkUgaAemhIeEQWVFJ1oZ20eL1tyYK6L0ABK
sd+p+AFeQNh5tqymzacLd2a17Ei9FS+7udfKcKIGdOhX5d4Y0ZNoSnLraXdmawDo
0SzMO3lNTdu11CKH/BsTlv20tuW2E18Ga4vFQE/MAOobHuSqZQ3D2PpUfBJ0jOc/
vtuVbCP5ABEBAAGJAjYEGAEIACAWIQQPLdGP4Gt767Na/UzwfRpig8QCtQUCX9Zy
0AIbDAAKCRDwfRpig8QCtYjyEACIgcNtLjbuoXoHqZbN9QueTCZDhUWSn8PRJqoP
v4CRQnlKkUasUBTl3nuqGDX8ONL+M1ogoZdL9ygiPswayim9/s03l2oVHg3SGXea
PCexXlaJm6cNu37MkPwYdVG0h0celQ5NrsE3olgIgmecczMKnrIEcyymbrGzQX65
5oJKo2O0PYhQC9MfJSypIWMhXdn1OWk3bs7EzFpqNqhzwQXyvkIu8OwvQlXbMu9d
HAm5kOOcfNmy+vDsH4yxeErt3GeXRAP7K9XevFPVrWL5HmT2aRmU93W4kfmwJ6zs
g8B8VjxvHt65bs/fDrZnCZQ4PCz9x6wA5GU5fgzeidNoiQAYWgqq7DXI0ZNJUNYF
iiNoZ4xhHmfHAp9ZQ361g5iOk+qhAIQXWimW9H2gJ/jjTSvRjhGZuh3bnETSAzbY
Ixgiuoshfn7DtvVmwIR+FVPbCG+oY0n1UhSVjXvUtbIiF533loUHYuXUqc3XRcuu
KkWuWiR1Wblia/SyzMTx855TQoH1WfYYWdEeX1vyBBez9Smh9JoLBh4POcyA0vYH
v0VEvfs8lOLJh1/mwi6z/bo1AGJwY+fnPaE57valIafxrPfzuIyiDwoU4a27wBhV
DRQAVfNG2IV1HI11lV5+pxnw9FiOs2b2DEsi6pUXh5j5KpL7E5Pi+QiKfFEnVMgl
o7SbWg===3i8i
-----END PGP PUBLIC KEY BLOCK-----